(Created page with "Category:Tools ==Scanning Options== {| ! width="5%" |'''Nmap Option''' ! width="6%" |'''Description''' |- |<code>10.10.10.0/24</code> |Target network range. |- |<code>-sn</code> |Disables port scanning. |- |<code>-Pn</code> |Disables ICMP Echo Requests |- |<code>-n</code> |Disables DNS Resolution. |- |<code>-PE</code> |Performs the ping scan by using ICMP Echo Requests against the target. |- |<code>--packet-trace</code> |Shows all packets sent and received. |- |<cod...") |
No edit summary |
||
| (11 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Tools]] | [[Category:Tools]] | ||
== | [[Category:Reconnaissance]] | ||
<section begin="Options"></section> | |||
=Resources= | |||
NMAP Script Directory | |||
<code>https://nmap.org/nsedoc/scripts/</code> | |||
=Notes= | |||
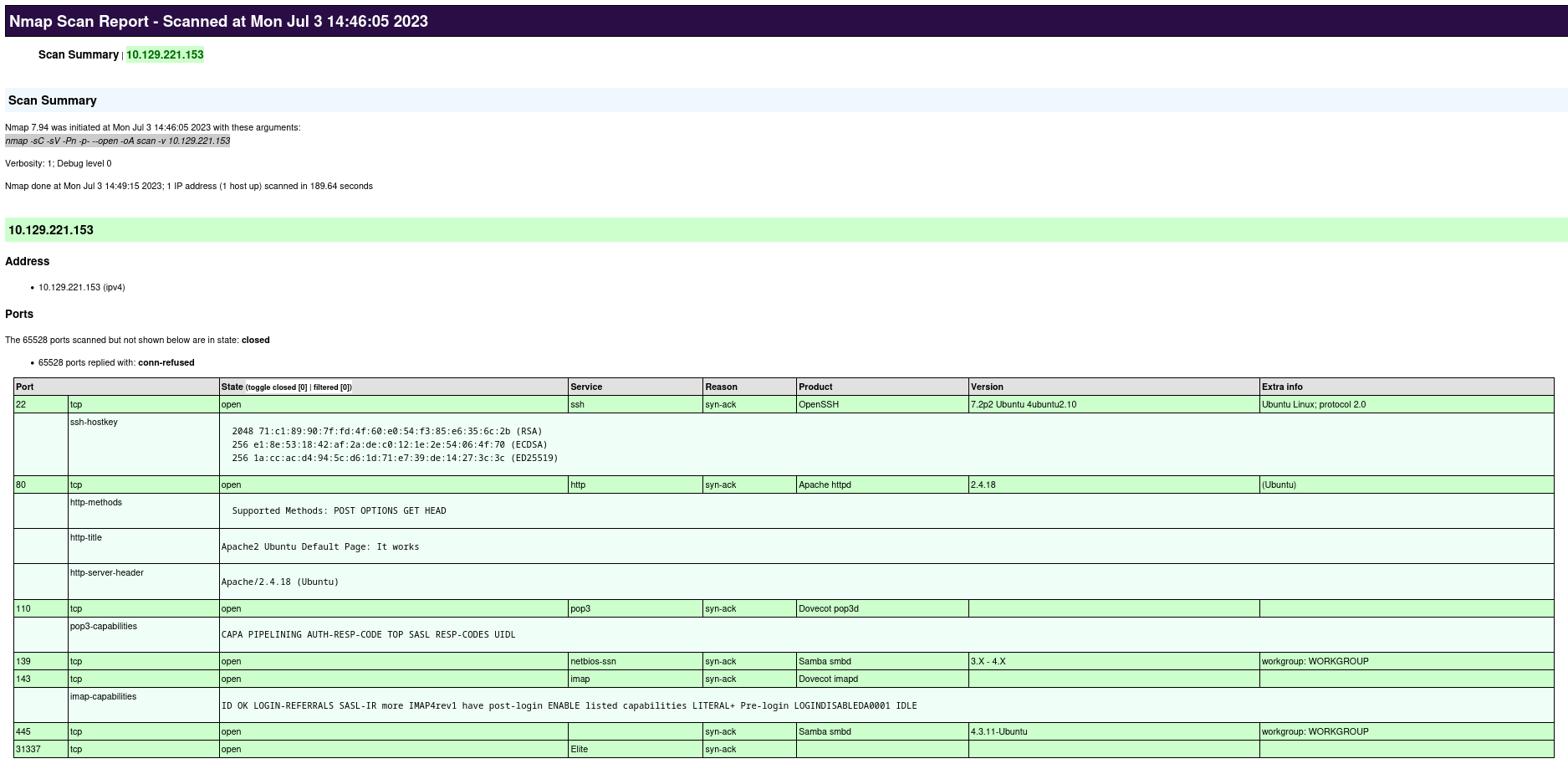
Convert xml scans to html files | |||
<code>xsltproc target.xml -o target.html</code> | |||
[[File:Nmap Scan.png|frameless|center|800x800px]] | |||
=Scanning Options= | |||
{| | {| | ||
! width="5%" |'''Nmap Option''' | ! width="5%" |'''Nmap Option''' | ||
! width="6%" |'''Description''' | ! width="6%" |'''Description''' | ||
|- | |- | ||
|<code>10.10.10.0/24</code> | |<code>10.10.10.0/24</code> | ||
| Line 22: | Line 31: | ||
|- | |- | ||
|<code>--packet-trace</code> | |<code>--packet-trace</code> | ||
|Shows all packets sent and received. | |Shows all packets sent and received. | ||
|- | |- | ||
|<code>--reason</code> | | <code>--reason</code> | ||
|Displays the reason for a specific result. | |Displays the reason for a specific result. | ||
|- | |- | ||
| Line 36: | Line 45: | ||
|Scan all ports. | |Scan all ports. | ||
|- | |- | ||
|<code>-p22-110</code> | | <code>-p22-110</code> | ||
|Scan all ports between 22 and 110. | |Scan all ports between 22 and 110. | ||
|- | |- | ||
| Line 60: | Line 69: | ||
|Perform a Script Scan with scripts that are categorized as "default". | |Perform a Script Scan with scripts that are categorized as "default". | ||
|- | |- | ||
|<code>--script <script></code> | | <code>--script <script></code> | ||
|Performs a Script Scan by using the specified scripts. | |Performs a Script Scan by using the specified scripts. | ||
|- | |- | ||
| Line 66: | Line 75: | ||
|Performs an OS Detection Scan to determine the OS of the target. | |Performs an OS Detection Scan to determine the OS of the target. | ||
|- | |- | ||
|<code>-A</code> | |<code>-A</code> | ||
|Performs OS Detection, Service Detection, and traceroute scans. | |Performs OS Detection, Service Detection, and traceroute scans. | ||
|- | |- | ||
|<code>-D RND:5</code> | | <code>-D RND:5</code> | ||
|Sets the number of random Decoys that will be used to scan the target. | |Sets the number of random Decoys that will be used to scan the target. | ||
|- | |- | ||
|<code>-e</code> | | <code>-e</code> | ||
|Specifies the network interface that is used for the scan. | | Specifies the network interface that is used for the scan. | ||
|- | |- | ||
|<code>-S 10.10.10.200</code> | |<code>-S 10.10.10.200</code> | ||
|Specifies the source IP address for the scan. | |Specifies the source IP address for the scan. | ||
|- | |- | ||
|<code>-g</code> | |<code>-g</code> | ||
| Line 82: | Line 91: | ||
|- | |- | ||
|<code>--dns-server <ns></code> | |<code>--dns-server <ns></code> | ||
|DNS resolution is performed by using a specified name server. | | DNS resolution is performed by using a specified name server. | ||
|} | |} | ||
<section end="Options" /> | |||
==Output Options | <section begin="Output" /> | ||
=Output Options= | |||
{| | {| | ||
| Line 91: | Line 101: | ||
! width="6%" |'''Description''' | ! width="6%" |'''Description''' | ||
|- | |- | ||
|<code>-oA filename</code> | | <code>-oA filename</code> | ||
|Stores the results in all available formats starting with the name of "filename". | |Stores the results in all available formats starting with the name of "filename". | ||
|- | |- | ||
|<code>-oN filename</code> | | <code>-oN filename</code> | ||
|Stores the results in normal format with the name "filename". | |Stores the results in normal format with the name "filename". | ||
|- | |- | ||
|<code>-oG filename</code> | | <code>-oG filename</code> | ||
|Stores the results in "grepable" format with the name of "filename". | |Stores the results in "grepable" format with the name of "filename". | ||
|- | |- | ||
|<code>-oX filename</code> | | <code>-oX filename</code> | ||
|Stores the results in XML format with the name of "filename". | |Stores the results in XML format with the name of "filename". | ||
|} | |} | ||
<section end="Output" /> | |||
<section begin="Performance" /> | |||
==Performance Options== | ==Performance Options== | ||
| Line 110: | Line 121: | ||
! width="6%" |'''Description''' | ! width="6%" |'''Description''' | ||
|- | |- | ||
|<code>--max-retries <num></code> | | <code>--max-retries <num></code> | ||
|Sets the number of retries for scans of specific ports. | | Sets the number of retries for scans of specific ports. | ||
|- | |- | ||
|<code>--stats-every=5s</code> | |<code>--stats-every=5s</code> | ||
| Line 120: | Line 131: | ||
|- | |- | ||
|<code>--initial-rtt-timeout 50ms</code> | |<code>--initial-rtt-timeout 50ms</code> | ||
|Sets the specified time value as initial RTT timeout. | |Sets the specified time value as initial RTT timeout. | ||
|- | |- | ||
|<code>--max-rtt-timeout 100ms</code> | |<code>--max-rtt-timeout 100ms</code> | ||
| Line 126: | Line 137: | ||
|- | |- | ||
|<code>--min-rate 300</code> | |<code>--min-rate 300</code> | ||
|Sets the number of packets that will be sent simultaneously. | |Sets the number of packets that will be sent simultaneously. | ||
|- | |- | ||
|<code>-T <0-5></code> | |<code>-T <0-5></code> | ||
|Specifies the specific timing template. | |Specifies the specific timing template. | ||
|} | |} | ||
<section end="Performance" /> | |||
Latest revision as of 11:28, 6 July 2023
Resources
NMAP Script Directory
https://nmap.org/nsedoc/scripts/
Notes
Convert xml scans to html files
xsltproc target.xml -o target.html
Scanning Options
| Nmap Option | Description |
|---|---|
10.10.10.0/24
|
Target network range. |
-sn
|
Disables port scanning. |
-Pn
|
Disables ICMP Echo Requests |
-n
|
Disables DNS Resolution. |
-PE
|
Performs the ping scan by using ICMP Echo Requests against the target. |
--packet-trace
|
Shows all packets sent and received. |
--reason
|
Displays the reason for a specific result. |
--disable-arp-ping
|
Disables ARP Ping Requests. |
--top-ports=<num>
|
Scans the specified top ports that have been defined as most frequent. |
-p-
|
Scan all ports. |
-p22-110
|
Scan all ports between 22 and 110. |
-p22,25
|
Scans only the specified ports 22 and 25. |
-F
|
Scans top 100 ports. |
-sS
|
Performs an TCP SYN-Scan. |
-sA
|
Performs an TCP ACK-Scan. |
-sU
|
Performs an UDP Scan. |
-sV
|
Scans the discovered services for their versions. |
-sC
|
Perform a Script Scan with scripts that are categorized as "default". |
--script <script>
|
Performs a Script Scan by using the specified scripts. |
-O
|
Performs an OS Detection Scan to determine the OS of the target. |
-A
|
Performs OS Detection, Service Detection, and traceroute scans. |
-D RND:5
|
Sets the number of random Decoys that will be used to scan the target. |
-e
|
Specifies the network interface that is used for the scan. |
-S 10.10.10.200
|
Specifies the source IP address for the scan. |
-g
|
Specifies the source port for the scan. |
--dns-server <ns>
|
DNS resolution is performed by using a specified name server. |
Output Options
| Nmap Option | Description |
|---|---|
-oA filename
|
Stores the results in all available formats starting with the name of "filename". |
-oN filename
|
Stores the results in normal format with the name "filename". |
-oG filename
|
Stores the results in "grepable" format with the name of "filename". |
-oX filename
|
Stores the results in XML format with the name of "filename". |
Performance Options
| Nmap Option | Description |
|---|---|
--max-retries <num>
|
Sets the number of retries for scans of specific ports. |
--stats-every=5s
|
Displays scan's status every 5 seconds. |
-v/-vv
|
Displays verbose output during the scan. |
--initial-rtt-timeout 50ms
|
Sets the specified time value as initial RTT timeout. |
--max-rtt-timeout 100ms
|
Sets the specified time value as maximum RTT timeout. |
--min-rate 300
|
Sets the number of packets that will be sent simultaneously. |
-T <0-5>
|
Specifies the specific timing template. |